
Festival of Phishes


Campus accounts have been targeted by a few scam and phishing emails this week. Examples are provided below. Do not reply to these emails or click on the links.
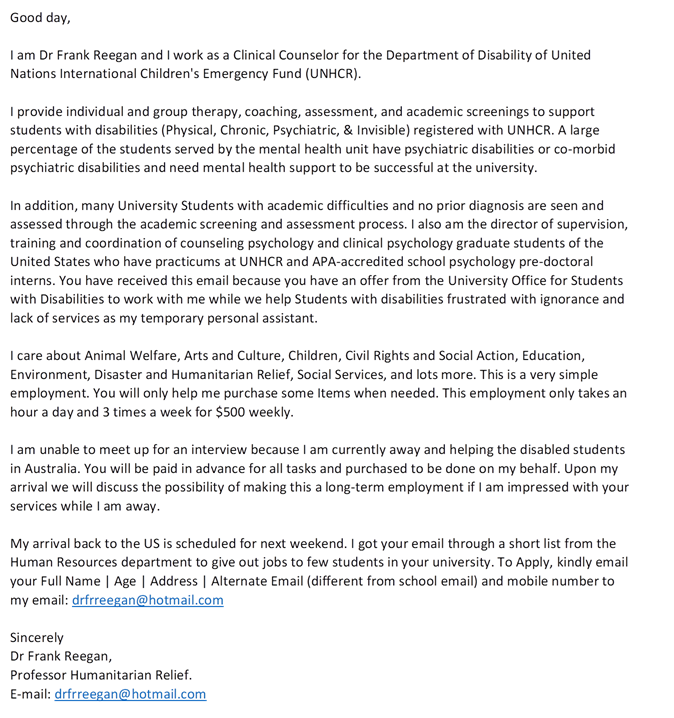
Unsolicited job offers are likely to be scams, especially if they’re offering to pay $150+/hour. Do not reply to this email and be cautious of requests for your personal information.
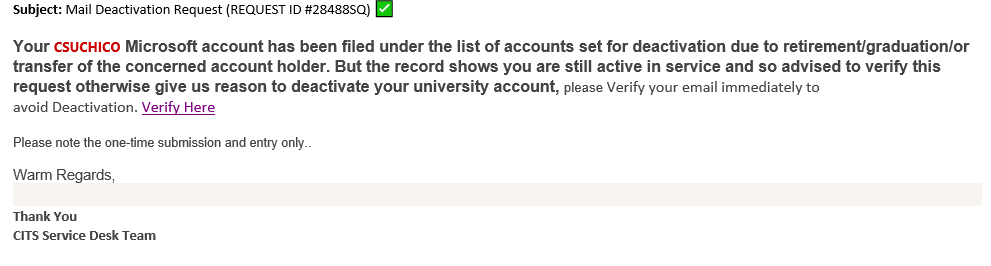
If you clicked on a link and provided your credentials you should use Account Center (via the Portal) to reset your password.
ISEC was able to remove scam emails from campus mailboxes, and the links used have been reclassified as phishing and blocked on campus networks. Any campus accounts used to send these messages have had their passwords reset.
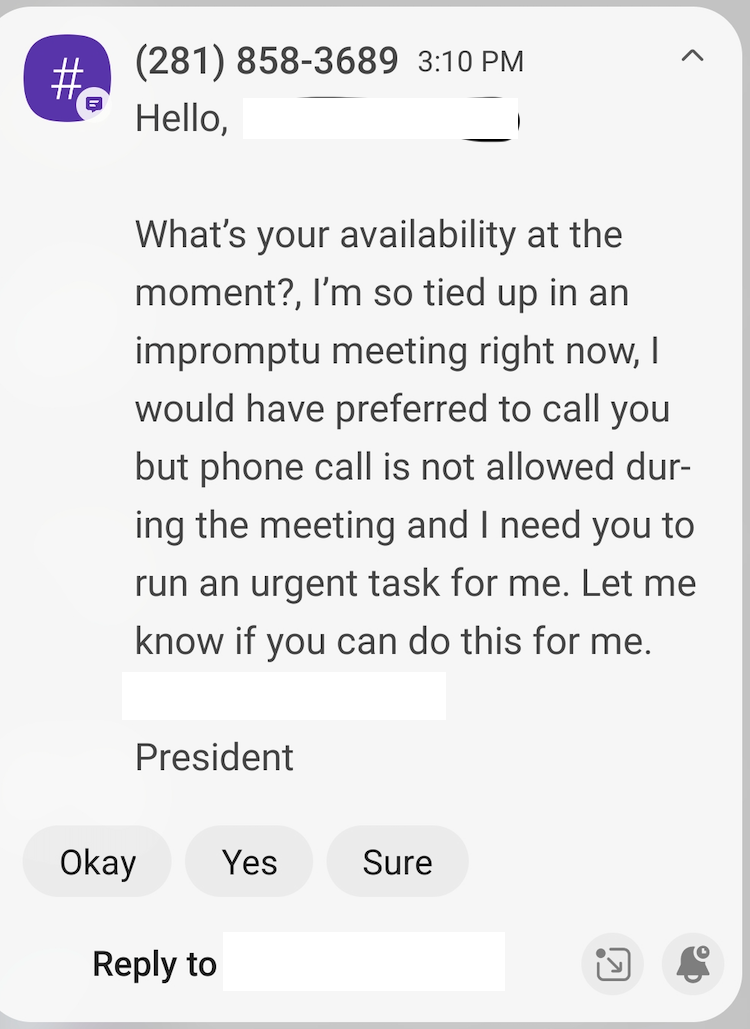
ISEC has received multiple reports by other CSU campuses about individuals receiving unsolicited text messages from unrecognized phone numbers masquerading as campus officials. If you have received a similar text message, please do not reply or respond to the message.
What is Smishing?
Smishing is a term used to describe phishing attempts and scams that use text messages or (Short Message Service) SMS as the primary attack platform. It is used to gather different types of personal information, including addresses, credit card information, and more.Spam texts (also known as phishing texts spam) are messages sent by hackers which attempt to get you to click on a link or divulge personal details such as banking information, credit cards, address, or even your social security number. Scam types vary, but they will usually make lucrative offers or pretend to be university administration to get you to respond.
Spam or fake text messages vary in form and content, but some key guidelines exist to identify text scams. Here are some common examples:
To enhance the security of campus managed computers IT is moving from Malwarebytes to Microsoft Defender on PCs and Macs. Mac users will notice a new icon on the menu bar and a new Microsoft Defender application. The transition for PCs will be seamless with enhanced security features enabled on the existing Defender installations. These enhanced features will help detect and remediate vulnerabilities and attacks in real time. Malwarebytes will be removed from all campus managed computers. The removal process should happen in the background and should not require user intervention.
The final day of Cybersecurity Awareness Month highlights data breaches, what they are, and how to identify them. Data breach costs in 2022 have increased 2.6% for an average cost of $4.35 million. It is vital that all members of the Chico State community to do their part to ensure cyber safety.
You can find more information about Week 5 of Cybersecurity Month at https://www.csuchico.edu/isec/2022-cyber-security-awareness/week5-cyber-security-awareness-2022.shtml
Week 4 is all about identifying Phishing. Phishing is when criminals use fake emails to lure you into handing over your personal information or installing malware on your device. It’s easy to avoid a phishing email, but only once you know what to look for.
You can find more information about Week 4 of Cybersecurity Month at https://www.csuchico.edu/isec/2022-cyber-security-awareness/week4-cyber-security-awareness-2022.shtml
When was the last time you applied patches for your device? Always keep your software updated when updates become available and don’t delay. These updates fix general software problems and provide new security patches to protect your systems from being comprised.
You can find more information about Week 3 of Cybersecurity Month at https://www.csuchico.edu/isec/2022-cyber-security-awareness/week3-cyber-security-awareness-2022.shtml
Creating, storing, and remembering passwords can be challenging for all of us online, but the truth is that utilizing unique and strong passwords is your first line of defense against cybercriminals and data breaches. It has never been easier to maintain your passwords with secure, free, and simple-to-use password managers. With a few moments of forethought today, your online accounts can remain safe for years to come.
LastPass is available to students and employees: https://support.csuchico.edu/TDClient/1984/Portal/KB/?CategoryID=18114
You can find more information about Week 2 of Cybersecurity Month at https://www.csuchico.edu/isec/2022-cyber-security-awareness/week2-cyber-security-awareness-2022.shtml
Cybersecurity Awareness Month is a global effort to help everyone stay safe and protected when using technology whenever and however you connect. The theme for the month is “See Yourself in Cyber,” and Chico State is proud to support this online safety and education initiative in October. The cybersecurity and digital privacy of our employees and students are important at Chico State. Throughout October, the Information Security Team will share activities and awareness materials, and each week will focus on a different theme. Students, faculty, and staff can find more information on upcoming events and themes at https://www.csuchico.edu/isec/2022-cyber-security-awareness/index.shtml.
This year the Chancellor’s Office is sponsoring a Cybersecurity Poster contest. The deadline for submissions is December 1st.
Cybersecurity Awareness Month is co-led by the National Cyber Security Alliance and the Cybersecurity and Infrastructure Agency (CISA) of the U.S. Department of Homeland Security.
Week 1: Fear Factor or Multi-Factor? Authenticate to Mitigate
Multi-factor authentication (MFA) is also known as two-factor authentication (2FA) and two-step verification. No matter what you call it, multi-factor authentication is a security measure that requires anyone logging into an account to navigate a two-step process to prove their identity. It makes it twice as hard for criminals to access an online account. When it’s available, always turn it on because it’s easy to do and dramatically increases your security. This is a great way to See Yourself in Cyber!
You can find more information about Week 1 at https://www.csuchico.edu/isec/2022-cyber-security-awareness/week1-cyber-security-awareness-2022.shtml
The LA Unified School District experienced a debilitating ransomware attack over the weekend, and several advisories have been released this week that have reported similar events targeting the education sector. Our Information Security Team and various other Division of IT Teams are actively monitoring the situation and staying up to date with the recommended compensating controls by the cybersecurity community. As details evolve, we wanted to share some helpful tips:
NPR’s reporting on the incident can be found at https://www.npr.org/2022/09/07/1121422336/a-cyberattack-hits-the-los-angeles-school-district-raising-alarm-across-the-coun